The Concept of Zero-Trust
 To allow for near-future work
models, where employees can bring their own mobile devices into the
workplace, where “work from home” is
standard practice, and where the Data Center is being virtualized and services
abstracted to external third party providers,
the Security Industry is rethinking the traditional concepts of boundaries and perimeters.
To allow for near-future work
models, where employees can bring their own mobile devices into the
workplace, where “work from home” is
standard practice, and where the Data Center is being virtualized and services
abstracted to external third party providers,
the Security Industry is rethinking the traditional concepts of boundaries and perimeters.
The
concept of Zero-Trust is an approach to network and device security that places security at the core of the network and makes it central to all
network transactions.
This
security
centric approach advocates a number of principles to design a secure and
flexible network that can protect against modern malware and threats.
Key
to
this design is the transformation from classical security overlay which simply
inspects packets destined to and from the Internet, to ensuring every packet is
securely delivered to its destination.
TheZero Trust model provides an innovative data-centric approach to security that protects against
sophisticated and targeted attacks.
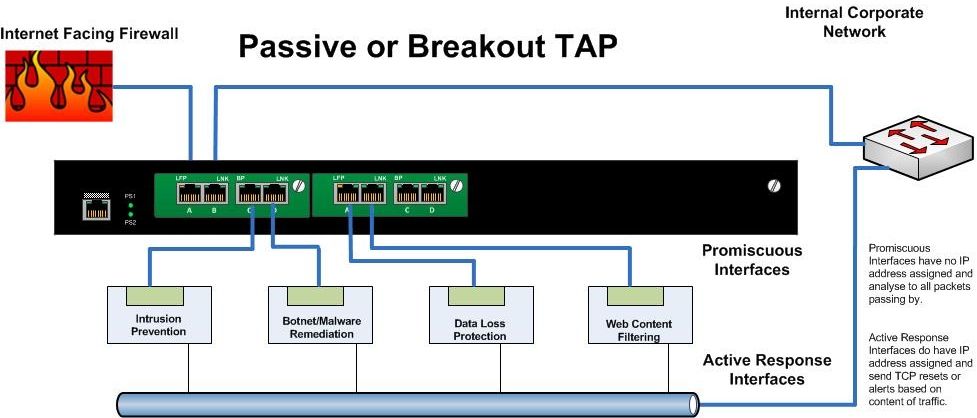
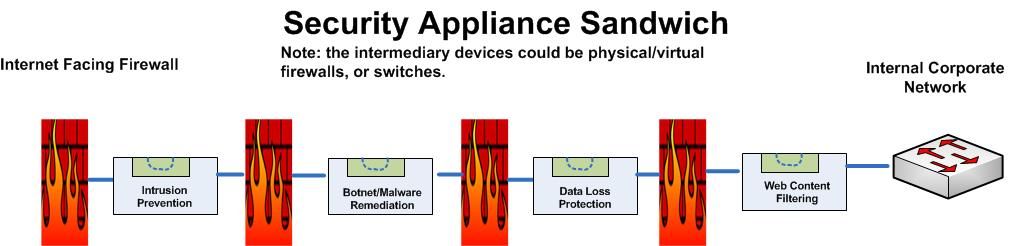
Regardless of the reason, your data center is expanding beyond your bricks and mortar controls. Many call this the Shrinking Perimeter. (Here, and Here, and Here,) Firewalls at the edge of your network are no longer adequate, and provide for a false sense of comfort.
Empowered
users
are accessing the network from a variety of devices (e.g., laptops, tablets,
and smart phones) and from a variety of locations.
The expectation of anytime anywhere “workspaces” for these users enable new gains in productivity, but also leads to new security challenges in differentiating access based on user, application, device-type or access type (wired, wireless, VPN).
A typical "Data Center" is constantly under threat, both from
external sources as well as internal entities.
What is "Host Protection"?
A “Host Protection”
service must ensure the integrity of all resources within the system it is
protecting. This would include
monitoring of and prevention against unwanted or malicious Network
traffic coming in and out of the host, monitoring and management of file
integrity, memory integrity, and in the case of Windows Servers, registry integrity.
Host protection will employ
centrally managed rules and profiles to ensure that applications on the host
behave appropriately and that user and service accounts only
have appropriate access to files and applications through whitelisting
and blacklisting.
A Host Protection Service must:
•Operate on the significant majority
of our Host Operating Systems, and support all of our existing Database and
Middleware
•Protect against Zero-Day malware
and malicious actor attacks.
•Prevent unauthorized
changes or actions, even if the perpetrator has administrative rights.
•Enable demonstrable change
control on mission-critical systems.
•Centralize configuration
protection across the enterprise, reducing administrative burden.
•Support a
library of pre-defined rules that recognize common security events.
•Support policies across
logical groups of hosts, helping to ensure the appropriate level of security and ease
administrative burden.
•Run pre-defined and customized
reports on policies and security events enterprise-wide across heterogeneous
systems.
•Automatically trigger alerts and
actions, based on pre-defined thresholds, when an event matches a rule.
•Record the event in a centralized corporate
SEIM.
What is considered a Host?
In the simplest terms, a “Host” is just a network connected
server that provides services to other systems.
These services may include database, mail, web, file share, print, etc…
- A host can be physical or virtual, and may run any of a dozen operating systems.
- A host typically will have additional software added to provide it’s specific functionality. This may include various commercial database and/or application server packages from a multitude of vendors.
- A host will generally have a specific purpose or “role” within the data center which would be defined by it’s configuration and/or applications/services running on it.
- Similar hosts may be “clustered” together to provide a single service for performance or availability reasons.
- Hosts may be grouped together by similar role
- Hosts that work together to provide a specific service may be grouped together
- Hosts that belong to a specific Business Unit may be grouped together
A managed host may reside anywhere
that connectivity and general network security is provided. This includes data center, branch/campus, telco
service provider, 3rd
party business partner, hosting provider or cloud service provider.
Regardless of Operating System, Almost all Servers are
comprised of the above layers.
All layers above the Operating System kernel are potential places for vulnerabilities, and exploitation. A complete Host Protection Service must take all of these into account.
Protecting a Heterogeneous Environment
Any
system or service devised to protect a typical data center environment must be
all-encompassing.
Broad Spectrum of Host Operating
System coverage:
- Any Host protection system deployed must operate and protect the majority of Operating Systems that can be found within the environment. This includes but is not limited to Microsoft Windows Server, IBM AIX , HPUX, Solaris, Linux, VMware, Xen, Microsoft HyperV
Broad Spectrum of Database
Server coverage:
- Any Host protection system deployed must operate and protect the majority of Database Systems that can be found within the environment. This includes but is not limited to Microsoft SQL Server, Oracle SQL, Sybase, IBM DB2, Ingres, PosGreSQL, MySQL,
•Broad Spectrum of Application
Server coverage:
- Any Host protection system deployed must operate and protect the majority of Application Servers and Frameworks that can be found within the environment. This includes but is not limited to Microsoft Active Directory, Exchange, SharePoint, and ISA, WebLogic, Oracle, WebSphere, Jboss, IBM Domino, Java, ASP.Net, PHP
Broad Spectrum of Web
Server
coverage:
- Any Host protection system deployed must operate and protect the majority of Web Servers that can be found within the environment. This includes but is not limited to Microsoft IIS, Apache, Tomcat, Weblogic, Oracle
Host Protection - Operating System Layer
- File Integrity Monitoring and Prevention:
- Identify changes to files in real-time, including who made the change and what changed within the file.
- Memory Integrity Monitoring and Prevention:
- Identify in real-time, any attempt to modify or corrupt memory outside of the boundaries of that owned or managed by a specific application or service.
- Registry Integrity Monitoring and Prevention:
- Identify changes to Windows Registry settings in real-time, including who made the change and what changed within the registry.
- Device Control:
- Identify, prevent and alert on attempts to access system devices which are outside of a particular security profile.
- Configuration Monitoring:
- Identify policy violations, suspicious administrators or intruder activity in real-time.
- Targeted Prevention Policy:
- Respond to server incursion or compromise immediately with quickly customizable hardening policies.
- Granular Intrusion Prevention Policies:
- Protect against zero day threats and restrict the behavior of approved applications even after they are allowed to run with least privilege access controls.
- File, system and admin lock down:
- Harden virtual and physical servers to maximize system uptime and avoid ongoing support costs for legacy operating systems.
Host Protection - Network Layer
A Host Protection Service must be
able to provide a means to identify and control network traffic into and out of
the host in question.
Centralized management,
reporting, alerting of standard Layer 3 firewall functionality
is mandatory
•Source / Destination / Port /
Service for each packet must be
validated
•Stateful inspection is “nice to
have” but not a requirement
Centralized management,
reporting, alerting of Layer 4 through 7 “Application
Firewall” functionality is mandatory for systems not protected by Network based WAFs. Depending on
the purpose of the host, the WAF profile will differ:
•At minimum recognize and protect
against OWASP top 10 application vulnerabilities
Intrusion Prevention through
any of signature / whitelist / blacklist or heuristics, identify malicious or
malformed traffic, and based on policy settings: prevent, log, and alert.
Host Protection - Application Layer
A Host Protection Service must be able to provide a means to identify and control appropriate access within and between applications…..
A host protection service must be
able to monitor/collect/report on all resources that an
application uses over a period of time to define a “baseline”
for
appropriate behavior or functionality.
These resources include, but are not limited to:
- Files
- Folders
- registry settings
- device drivers
- Libraries
- network connections
- service accounts
Once the baseline has been set, any
deviation from that must get escalated for review and/or remediation.
This baseline can them be used as a
template for other hosts running this same application.
A profile or role can be made,
based on this baseline, and a centralized policy defined to manage all hosts
that use this template.
Host Protection - Database Layer
A
Host Protection Service must be able to proactively prevent or provide
remediation for security risks to database systems.
These
risks include, but
are not limited to:
- Unauthorized or unintended activity or misuse by authorized database users, database administrators, or network/systems managers.
- Unauthorized or unintended activity or misuse by or by unauthorized users
- Unauthorized or unintended privilege escalation
- Malware infections causing unauthorized access, leakage or disclosure of personal or proprietary data, deletion of or damage to the data or programs, interruption or denial of authorized access to the database, attacks on other systems
- Design flaws and programming bugs in databases and the associated programs and systems, creating various security vulnerabilities
Host Protection - Web Layer
According to OWASP (http://www.owasp.org) and SANS ( http://www.sans.org) The top Web Server vulnerabilities include:
|
|
OWASP is
the emerging standards body for Web application security. In particular they
have published the OWASP
Top 10
which describes in detail the major threats against web applications. The Web
Application Security Consortium (WASC) has created the Web Hacking
Incident Database[8] and
also produced open source best practice documents on Web application security.
Host Protection - Managing Profiles
A
Host Protection Service must be able to centrally manage security profiles
and templates, proactively alert on deviations, accept real-time updates from
external threat intelligence providers, and feed a centralized SIEM or SOC.
Management
of security profiles will allow for granular nesting of roles/profiles
For
example:
- Nested security profiles, akin to Active Directory’s “Group Policy” management will enable quick access and visibility to host assets by Owner, Role, or Location
- A high level role would be assigned to “Operating System Platform”
- A nested role would be assigned to SPECIFIC Operating Systems (Windows Server 2003, Windows Server 2007, AIX 5.3, AIX 6.0, HPUX 11…) to refine control
- A high level role would be assigned to each Database System Platform
- A nested role would be assigned to SPECIFIC Database Systems to refine control
- A nested role would be assigned to Critical Database Systems to refine control
- A high level role would be assigned to each Application Type
- A nested role would be assigned to SPECIFIC Application Instances to refine control
- A high level role would be assigned to each Web Server Platform
- A nested role would be assigned to SPECIFIC Web Server types to refine control
- A nested role would be assigned to Critical Web Servers to refine control
Security profiles can be nested and grouped by role, owner, or location.
To be effective, a Host Protection Service must be managed centrally, receive
live threat and signature updates, and report into a SEIM or SOC in real-time.
So? Who are the players in this field?
Symantec Critical System Protection
- To date, Symantec CSP provides the widest coverage for server roles
across the most Operating Systems - Both Physical and Virtual. Their
System Protection Console cleanly integrates their Security and Malware
product suites into a single pane of glass.
TripWire Enterprise File Integrity Monitor - TripWire has been the industry leader in this space for over a decade, and is perfect for small to medium enterprises.
McAfee File Integrity Monitor - McAfee provides a suite of tools that are well integrated for protecting Windows Based Servers and Databases..
IBM Tivoli Virtual Server Protection - VMware ESX protection suite.
SafeNet Data Protection Suite
NewNetTechnologies NNT
Splunk Change Monitor
McAfee File Integrity Monitor - McAfee provides a suite of tools that are well integrated for protecting Windows Based Servers and Databases..
IBM Tivoli Virtual Server Protection - VMware ESX protection suite.
SafeNet Data Protection Suite
NewNetTechnologies NNT
Splunk Change Monitor
References:
Further Reading:
http://www.novell.com/docrep/2010/03/Log_Event_Mgmt_WP_DrAntonChuvakin_March2010_Single_en.pdf
http://www.acunetix.com/websitesecurity/webserver-security/
http://www.symantec.com/page.jsp?id=protection-center
http://msmvps.com/blogs/ulfbsimonweidner/archive/2007/09/25/protect-objects-from-accidential-deletion-in-windows-server-2008.aspx
http://eval.veritas.com/mktginfo/enterprise/white_papers/ent-whitepaper_protecting_active_directory.pdf
http://www.sans.org/reading_room/analysts_program/mcafee-server-protection-june-2010.pdf
http://www.newnettechnologies.com/tripwire-alternative.html?gclid=CO3A8cn1uLUCFShgMgodLloAtw
McAfee Total Protection for Endpoint Datasheet
McAfee Total Protection for Virtualization Solution Breif Datasheet
3rd party List of System Integrity Tools:
https://mosaicsecurity.com/categories/83-system-integrity-tools?direction=desc&sort=products.name