As I've ranted... er... discussed in my previous blogs; we, as an industry, have spent the past two decades building logical security controls at the perimeter where our corporate network interfaces with either the Internet or Business Parner networks.
According to the 2012 Verizon Data Breach Investigations Report , and contrary to popular belief, 94% of all data compromised involved servers.
Moving forward, we must assunme that our internal network has already been compromised, or at minimum is quite vulnerable, and that to protect the corporate data assets, we must move our security controls as close as we can to that data.
- Prevent Unauthorized Access to critical assets.
- Prevent Unauthorized Changes to critical assets even for those with legitimate access.
- Protect against Zero-Day Malware attacks.
- File Integrity Monitoring
- Process Monitoring
- System Registry Monitoring
- Local Firewall
- Intrusion Detection
- Intrusion Prevention
- Comprehensive Logging
- Security Policy Management
Note: This discussion is completely agnostic to whether a server is physical or virtual. The requirements are identical.
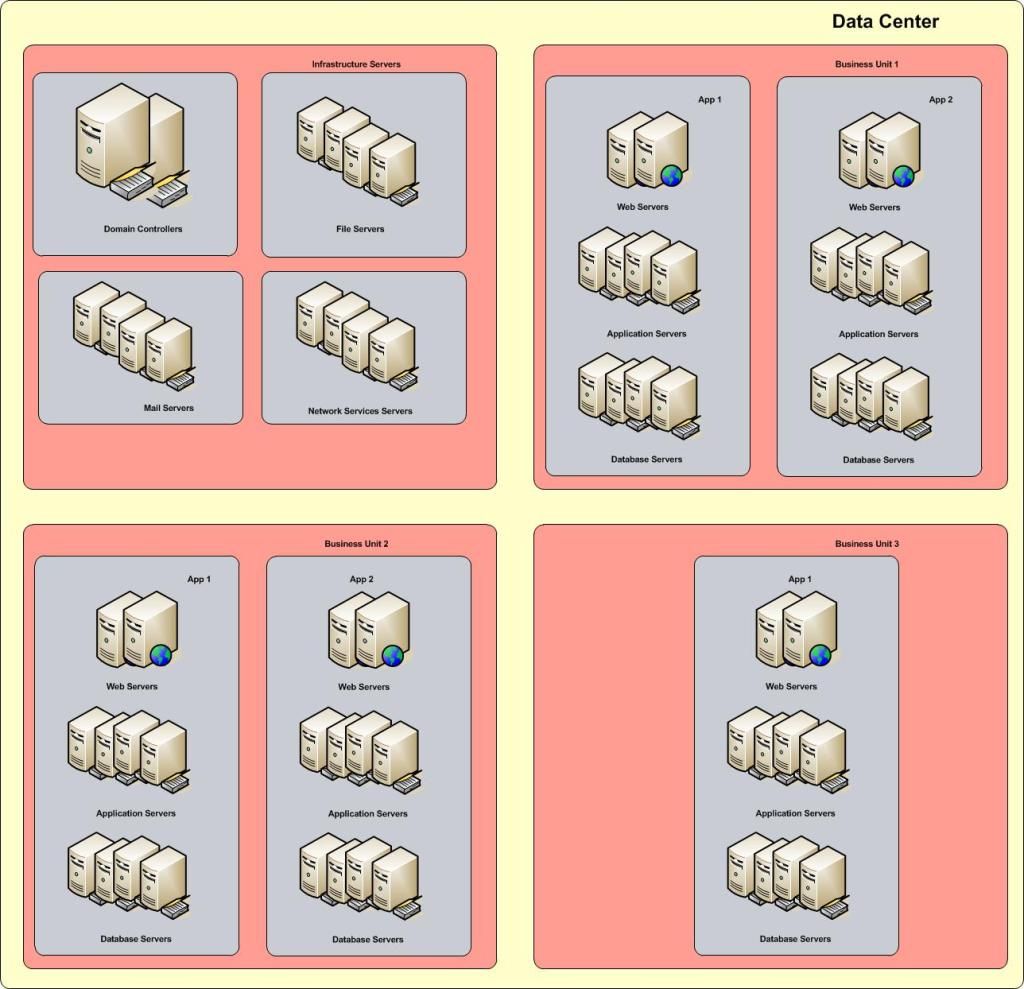
To start, create specific server "roles". A server role, defines it's function or purpose within your network. A role does not have to be OS specific - Windows/UNIX/Linux all provide for every role in the stack.
Any particular server could be an Authentication Server such as an Active Directory Domain Controller. It could be an Infrastructure Server, such as mail, ftp, or DNS. It could be a Database or File Server. It could be An Application or Web Server.
Typically, you will find that any one server may host several roles. In any case, you will want to create and apply a consistent Policy Template that will define the protection model for each role. In the template, you would identify resources to protect, such as directories, files, registry keys that are used to configure, maintain, and operate that application. (All commercial products in this space provide hundreds of such templates "out-of-the-box")
Once you have identified the roles, you will want to group your server assets into units, possibly by Line of Business (My line of business depends on these servers), or by Application (this application uses these web servers, these app servers, and this database server), or both. This way, you can create policies establishing the allowed channels of communication.
(App1 webservers can only talk to App1 application servers on tcp ports 80 and 443, and App1 application servers can only talk to App1 database servers on tcp port 1433)
By putting the security policies locally on the servers, close to the data, you significatly reduce the potential for data exfiltration. That said, this is not a Data Loss Prevention solution unto it's own, as it is not aware of the context of the data it is protecting, but can provide valuable feeds into your DLP infrastructure.
Of course this would not be complete without talking about the basics of creating a hardened server in the first place.
- Patch, patch, and patch....
- Disable/remove/rename default administrator accounts - at the OS, Application, and Database layer
- Turn off / Disable / Uninstall all services not required for the role of the server
- Place your Application Server / Database Server files on a separate volume from your OS
- Where possible, enable logging for everything
- Consult your vendor for additional recommendations per server role.
Examples of like Server Roles: (Apologies if I left out your personal favorite!)
- Active Directory Domain Controllers / LDAP Servers
- Radius Servers / Reverse Proxy
- NIS/Yellow Pages servers / RACF/ACF2
- Domino Name and Address Book
- VPN / Access Gateways (Citrix) / RSA 2 factor
File and Database Servers:
- Microsoft SQL / Oracle / DB2 / Sybase
- MySQL / PostgreSQL / NoSQL
- CIFS / SBM / Samba
Web Servers:
- Microsoft IIS / Apache / Zeus
So? Who are the players in this field?
Symantec Critical System Protection - To date, Symantec CSP provides the widest coverage for server roles across the most Operating Systems - Both Physical and Virtual. Their System Protection Console cleanly integrates their Security and Malware product suites into a single pane of glass.
TripWire Enterprise File Integrity Monitor - TripWire has been the industry leader in this space for over a decade, and is perfect for small to medium enterprises.
McAfee File Integrity Monitor - McAfee provides a suite of tools that are well integrated for protecting Windows Based Servers and Databases..
IBM Tivoli Virtual Server Protection - VMware ESX protection suite.
SafeNet Data Protection Suite
NewNetTechnologies NNT
Splunk Change Monitor
McAfee File Integrity Monitor - McAfee provides a suite of tools that are well integrated for protecting Windows Based Servers and Databases..
IBM Tivoli Virtual Server Protection - VMware ESX protection suite.
SafeNet Data Protection Suite
NewNetTechnologies NNT
Splunk Change Monitor
Further Reading:
http://www.novell.com/docrep/2010/03/Log_Event_Mgmt_WP_DrAntonChuvakin_March2010_Single_en.pdf
http://www.acunetix.com/websitesecurity/webserver-security/
http://www.symantec.com/page.jsp?id=protection-center
http://msmvps.com/blogs/ulfbsimonweidner/archive/2007/09/25/protect-objects-from-accidential-deletion-in-windows-server-2008.aspx
http://eval.veritas.com/mktginfo/enterprise/white_papers/ent-whitepaper_protecting_active_directory.pdf
http://www.sans.org/reading_room/analysts_program/mcafee-server-protection-june-2010.pdf
http://www.newnettechnologies.com/tripwire-alternative.html?gclid=CO3A8cn1uLUCFShgMgodLloAtw
3rd party List of System Integrity Tools:
https://mosaicsecurity.com/categories/83-system-integrity-tools?direction=desc&sort=products.name
http://www.newnettechnologies.com/tripwire-alternative.html?gclid=CO3A8cn1uLUCFShgMgodLloAtw
3rd party List of System Integrity Tools:
https://mosaicsecurity.com/categories/83-system-integrity-tools?direction=desc&sort=products.name


"3rd party List of System Integrity Tools" link is broken
ReplyDelete