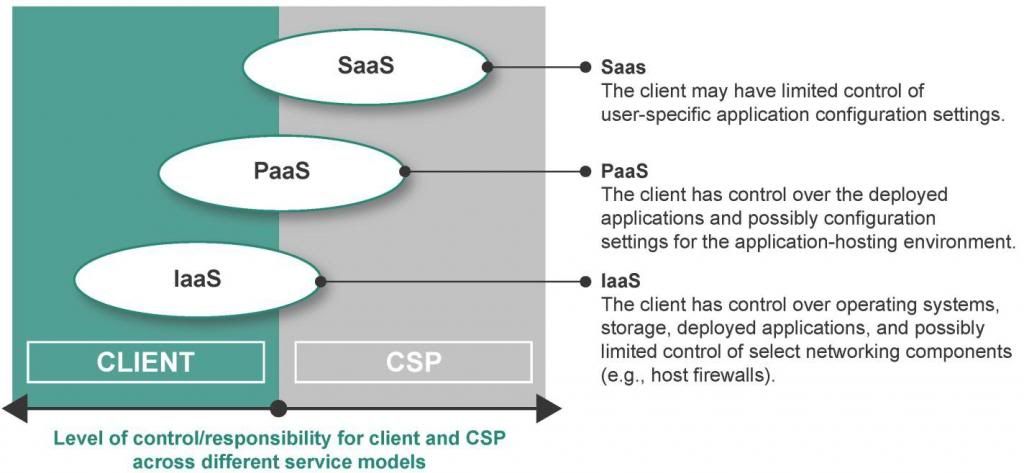
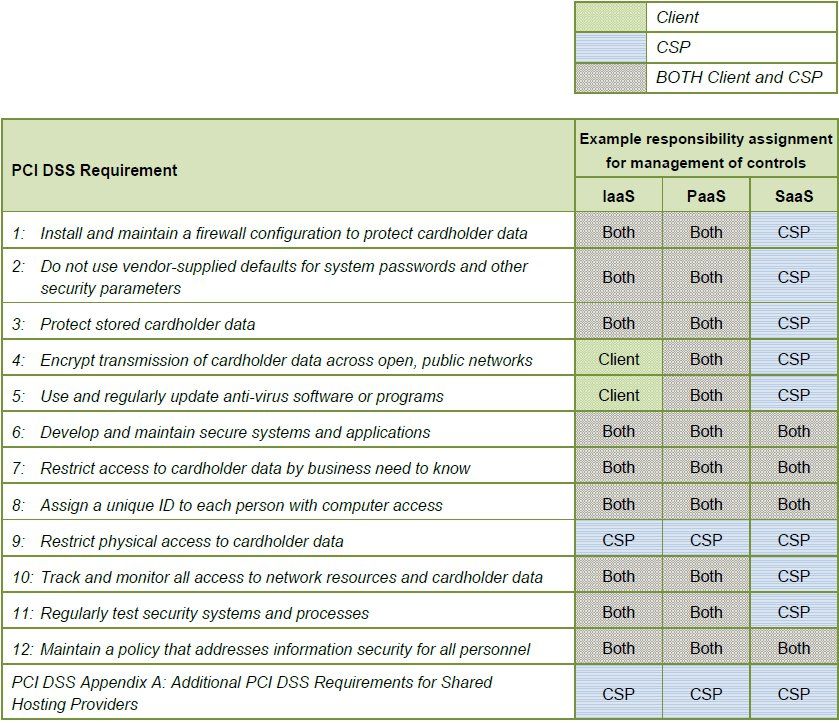
Last year, I wrote about a new Canadian company that had entered the Compliance Appliance market space. Blueline Data had developed a tokenization gateway that would help you define and isolate your PCI compliance scope boundary. This isolation was not only for Point Of Sale and Web Merchant portals (Shopping portal), but for Telephony and Unified Communications traffic as well! This was a revolutionary step in this industry. Several other companies had tokenization systems available for structured and/or unstructured data, however no one had a viable solution that would also cover voice and unified communications.
Last year, I wrote about a new Canadian company that had entered the Compliance Appliance market space. Blueline Data had developed a tokenization gateway that would help you define and isolate your PCI compliance scope boundary. This isolation was not only for Point Of Sale and Web Merchant portals (Shopping portal), but for Telephony and Unified Communications traffic as well! This was a revolutionary step in this industry. Several other companies had tokenization systems available for structured and/or unstructured data, however no one had a viable solution that would also cover voice and unified communications.
A lot has gone on in the past year, and I decided to revisit them, to see where their technology has progressed...
Last year, Forrester issued a paper defining the requirements necessary to secure data into the future, and discussing the technologies that will get us there. The Document titled "TechRadar™: Data Security, Q2 2014", states clearly that you need to:
- Restrict and strictly enforce access control to data. This includes denying access to unauthorized persons or blocking their attempts to gain access.
- Monitor and identify abnormal patterns of network or user behavior. This includes tools that analyze traffic patterns and/or monitor user behavior to detect suspicious anomalies (e.g., improper or excessive use of entitlements such as bulk downloads of sensitive customer information).
- Block exfiltration of sensitive data. These are tools or features of tools that detect, and optionally prevent, violations to policies regarding the use, storage, and transmission of sensitive data.
- Render successful theft of data harmless. Once you’ve identified your most sensitive data, the best way to protect it is to “kill” it.6 “Killing” data through encryption, tokenization, and other means renders the data unreadable and useless to would-be cybercriminals who want to sell it on the underground market.
The first three have been the bread and butter of the Information Security industry for the past 20 years or so. From firewalls and both signature and heuristics based Intrusion Detection/Prevention, to Data Loss Prevention systems, the industry has been diligently protecting our perimeters.
 To properly provide security through tokenization, one must be able to implement it not only on the server side for data at rest, but also for data in transit, as well as at the client side, such that the relevant sensitive data never even leaves the client's network.
To properly provide security through tokenization, one must be able to implement it not only on the server side for data at rest, but also for data in transit, as well as at the client side, such that the relevant sensitive data never even leaves the client's network.
It's that fourth one that I'm interested in here. "Render successful theft of data harmless." In other words, replace any valuable data such as Payment Card Info, Personal Health Info, Social Insurance Numbers, etc... with a "token" that has no value to would be thieves. These tokens can be made to preserve the format requirements of the original data, so as not to break backend processing, as well as including search/index criteria.
 To properly provide security through tokenization, one must be able to implement it not only on the server side for data at rest, but also for data in transit, as well as at the client side, such that the relevant sensitive data never even leaves the client's network.
To properly provide security through tokenization, one must be able to implement it not only on the server side for data at rest, but also for data in transit, as well as at the client side, such that the relevant sensitive data never even leaves the client's network.
What if, there was a service... APIs that could provide tokenization either at the client browser, or as data is passed to cloud apps?
I know that I'm not new to this train-of-thought, but the cost of non-compliance is growing exponentially.
Financial Damage can be insured against... Reputational damage cannot.
As I said... a lot has gone on in the past year. Blueline has matured from just providing on-premise gateway appliances, to hosting Compliance Services in the cloud.
Blueline is about to introduce several hosting options. You can still get on-premise control if that is what you desire, but that has been augmented with co-located gateway services as well as true Cloud based "Compliance as a Service" Tokenization/Encryption through APIs.
Another move that Blueline has made it to provide "Diskless Tokenization". Typically, tokenization services keep a very secure database in a cryptographic vault. This database would include a table of sensitive data to token pairs that are used to index and manage the tokens. Across the industry, customers have expressed concern over having this database, even though it is protected in a vault. Complaints from too much residual risk, to database latency in very large token pair tables (tens or hundreds of millions of pairs) have driven out an alternate solution.
Blueline has introduce a diskless solution that creates a "derived" token using a one time pad, without the need for the data/token pairs to be stored. These derived tokens, can be recalculated from some secret value that do not need to be stored in a database.
Blueline has created two new offerings:
 bluegrid™ is a turnkey solution for "Compliance in a Box". It is a standard 19" cabinet, consisting of a series of redundant "bluenodes™" that provide the various security, and compliance services required for a self contained Compliance DMZ. It can be installed in your own data center, or hosted externally for you. Applying the "Zero Trust" model, bluegrid™ encapsulates your sensitive application environment and provides a full security stack to protect that environment, from firewall, IPS, authentication store, tokenization, encryption, logging and storage.
bluegrid™ is a turnkey solution for "Compliance in a Box". It is a standard 19" cabinet, consisting of a series of redundant "bluenodes™" that provide the various security, and compliance services required for a self contained Compliance DMZ. It can be installed in your own data center, or hosted externally for you. Applying the "Zero Trust" model, bluegrid™ encapsulates your sensitive application environment and provides a full security stack to protect that environment, from firewall, IPS, authentication store, tokenization, encryption, logging and storage.A standard bluegrid™ rack would consist of a mix of the following bluenode™ appliances:
| bluenode tx - Traffic Manager (zero-impact deployment) bluenode dx - Data Gateway (financial network integration) bluenode cx - Cyber Vault (diskless tokenization, encryption) bluenode ix - Identity Manager (device and service access) bluenode ex - Event Manager (logging and event analytics) bluenode sx - Storage Block (low-latency shared storage) |
bluegrid™ can centralize and limit most of your PCI compliance scope to a single rack in the data center. (Point-of-Sale systems excluded)
 bluezone™ takes this one step further, providing a Cloud based Security Infrastructure - leveraging APIs to isolate the sensitive data outside of your IT environment and enabling secure financial or other confidential data processing and exposing the following security services:
bluezone™ takes this one step further, providing a Cloud based Security Infrastructure - leveraging APIs to isolate the sensitive data outside of your IT environment and enabling secure financial or other confidential data processing and exposing the following security services: - Tokenization–replacement of the original sensitive data with a risk-free replica for secure transmission, processing or storage
- Encryption–military-grade cryptographic protection of digital content
- Key Management–cryptographic key storage and lifecycle control
- Payment Gateway–secure real-time and offline merchant acquirer processing of tokenized e-commerce and m-commerce transactions
- Credit Scoring–secure personal or commercial credit check against a credit bureau, reference agency or central bank
- Address Verification–secure cardholder address validation
- Issuer Reconciliation–transaction batch transfer to issuer bank
- Digital Wallet–secure checkout for merchant commerce sites and mobile applications with the e-wallet payment method
bluezone™ can effectively remove most of your PCI compliance scope from your environment altogether.(Point-of-Sale systems excluded)
Forrester TechRadar report on Data Security Q2 2014 clearly shows Tokenization having "Significant Success" in securing sensitive data.
Resources:
http://security-musings.blogspot.ca/2015/03/tokenization-as-companion-to-encryption.html
http://www.itworldcanada.com/blog/toronto-upstart-brings-tokenization-protection-to-uc-web-pos/98109
https://www.forrester.com/TechRadar+Data+Security+Q2+2014/fulltext/-/E-res61547
http://www.mashery.com/blog/tokenization-and-api-gateways-future-mobile-commerce
http://www.mastercard.com/gateway/payment-processing/tokenization.html
https://www.pcicomplianceguide.org/how-you-can-use-tokenization-to-reduce-pci-scope/
http://www.protegrity.com/2012/02/differences-between-vault-based-tokenization-and-vaultless-tokenization/
http://www.protegrity.com/wp-content/uploads/2013/04/Protegrity-Vaultless-Tokenization-Fact-Sheet.pdf
https://securosis.com/blog/token-vaults-and-token-storage-tradeoffs
https://en.wikipedia.org/wiki/One-time_pad
https://en.wikipedia.org/wiki/Tokenization_(data_security)
https://www.voltage.com/technology/tokenization-and-key-management/hp-secure-stateless-tokenization/
http://www.trendmicro.co.uk/media/wp/kill-your-data-to-protect-whitepaper-en.pdf
http://www.bluelinex.com/trends.html
http://www.bluelinex.com/resources/blp204_osfi_compliance_sheet.pdf
http://www.bluelinex.com/resources/blp204_pci_compliance_sheet.pdf
http://www.bluelinex.com/resources/blp204_hipaa_compliance_sheet.pdf
http://searchcloudsecurity.techtarget.com/tutorial/PCI-and-cloud-computing-Cloud-computing-compliance-guide
http://www.crn.com/news/managed-services/300075263/2015s-big-opportunity-for-msps-compliance-as-a-service.htm
http://www.infoworld.com/article/2622986/risk-management/the-case-for-compliance-as-a-cloud-service.html