(http://www.itworldcanada.com/blog/toronto-upstart-brings-tokenization-protection-to-uc-web-pos/98109)
The standard Information Security mantra is to Protect Sensitive Data Where It Resides, but I posit that with the number of Security Breaches being publicized these days, we should quickly move to Remove Sensitive Data Where Not Required.
I know that I'm not new to this train-of-thought, but the cost of non-compliance is growing exponentially. Financial Damage can be insured against... Reputational damage cannot.
In a previous article, I spoke about the need for complementing industry standard Encryption with a process called Tokenization. While encryption is intended to hide the actual data in a manner that is reversible, tokenization replaces the sensitive data with a tag or token, preserving only the format or schema of the data.
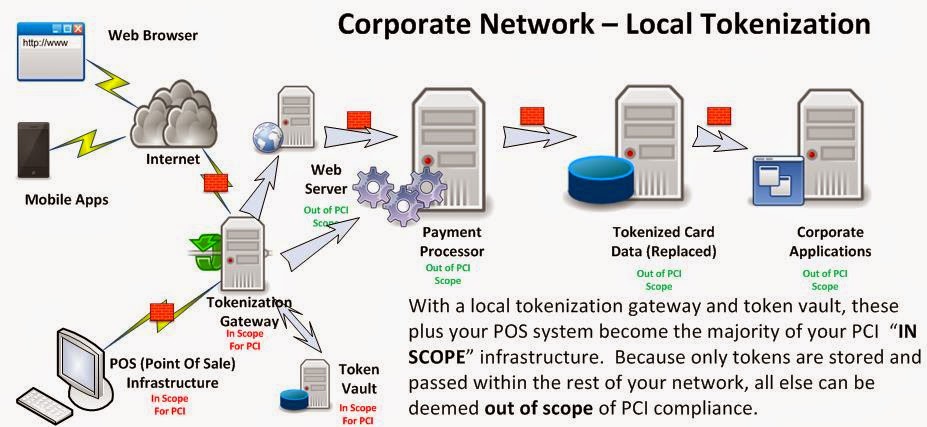
The Payment Card Industry has clearly stated that any piece of infrastructure that is accessible by network to those systems that either process or store PCI (Credit Card) Data are "in scope" for PCI compliance. This means that the scope an an annual compliance audit could essentially include every device on your network....
Many software companies have taken on portions of the tokenization challenge. Originally, they provided API's and libraries for developers to embed tokenization into applications, or bootstrap tokenization onto existing applications. These did little though to reduce the scope of your PCI compliance, and in many cases raised the complexity of the environment.
Next came the tokenization broker appliances, which were housed in your data center to communicate with your Point Of Sale and payment processing systems. Although this reduces scope and complexity of your PCI environment, it still leaves a large amount of your environment "in scope" for PCI, and the "crown jewels" were still onsite, albeit in a very robust data vault.
With a tokenization solution outsourced via a SaaS model, sensitive data such as credit card numbers are not stored in your system. There is nothing to obtain during a breach. Full stop. Let someone else take on the burden of PCI compliance.
Toronto's own Blueline Data has taken on the challenge, by creating a novel tokenization gateway solution that not only covers your Web and Point Of Sale transaction systems, but your Telephony and Unified Communications Infrastructure as well. In fact, you can define any type of digital data sequence to be protected for SOX / HIPAA / OSFI or any other regulatory requirement and tokenize it as well. They call their strategy "Assurance through Deterrence". By removing the sensitive data from your environment, they deter would-be attackers from investing in Advanced Persistent Attacks to breach your environment.
The PCI-DSS covers 6 areas of protection with 12 Specific Requirements. Blueline's unique offering covers 7 of these requirements, across 5 areas!
Their approach to format preserving and diskless tokenization at the perimeter, essentially creates a Zero Vector of Attack™ computing environment, which is easy to operate but not feasible to exploit.
I believe that their forward thinking initiative of providing tokenization services to non-traditional channels of data flow sets them aside from the competitors in this market. I'm anxious to watch this company flourish amid the weekly disclosures of Sensitive Data Breaches.
From the Blueline Data Website:
Blueline Data Products and Services
- Strategic Assessment – a review with your team to determine what Blueline Solutions would be most impactful with your business requirements and technology investments
- Solution Services – compliance delivery guidance and market insight (call center, financial services, healthcare, retail, etc.)
- Voice Gateway - encompasses security encryption around voice channels that send and receive sensitive data, to eliminate fraud by capturing, masking and encrypting confidential signaling information on the path. The encrypted sensitive datagrams are securely rendered to allow fully protected processing, eliminating the possibility of a call to get compromised.
- Retail Gateway - offers integration with any point-of-sale (POS) device in a secure and compliant manner, and allows point-to-point encryption of client's personal information from any payment media. This applies to any transaction or function where a client is required to use a payment terminal for credit or debit card processing expected to integrate with the backend data repository. There is no need for manual card data entry for proof of identity, payment guarantee or other purposes.
- Data Gateway - provides organizations with a single access point-of-presence to transaction services, such as secure banking and financial networks, mobile application payment delivery, or secure web bill presentment. It allows you centrally and uniformly govern all traffic of financial interest, whether it is exchanged between your partner organizations or with your clientele involved in the transaction flow. Sensitive data transfer is fully protected to meet the highest security and privacy standards.
- Data Vault - presents a conversion engine that takes any sensitive data element – whether it is SSN or SIN number, driver's license, credit or debit card, or patient record – and encrypts such information in a format-preserving manner. The data is tokenized and optionally stored in a secure "digital vault" that you can access as you need, provided that sufficient privileges are presented. It fully removes sensitive payment and personal information from your computing systems and digital media.
References:
PCI Security Standards: Information Supplement: PCI DSS Tokenization Guidelines
SANS: Six Ways to Reduce PCI DSS Audit Scope by Tokenizing Cardholder data
http://bluelinex.com/resources/blp204_pci_compliance_sheet.pdf
Blueline Services: Data Tokenization
Securosis: Understanding and Selecting a Tokenization Solution
Shift4: A detailed look at tokenization and it's Advantages over Encryption
TokenEX: Outsourcing Tokenization vs. On-Premise Data Security
http://www.mashery.com/api-gateway/tokenization
http://www.bankinfosecurity.com/whitepapers/using-pci-dss-criteria-for-pii-protection-w-947
Payment Card Industry (PCI) Data Security Standard
Protegrity Tokenization Securing Sensitive Data for PCI, HIPAA and Other Data Security Initiatives
Protegrity: Vaultless Tokenization
Protegrity: Vaultless Tokenization Fact Sheet.
Cybersource: Reducing PCI Compliance Scope: Take the Data Out
Intel: PCI DSS Tokenization Buyer’s Guide